Pass-Back-Attack: From Default Printer Credentials to Domain Admin
Looking at Pass-back-attacks & how to exploit trust relationships between devices that are generally considered benign.
The tail of a Xerox pass-back-attack. How to exploit trust relationships between devices that are generally considered benign and critical systems.
The attack I'm about to show you is not specific to the Xerox printers. This is a weaknesses impacting a large majority of off-the-shelf IoT devices. This type of attack is an attack where we direct an MFP device into authenticating via LDAP or SMB against a rogue system rather than the expected server. In essence we're leveraging the trust relationships between devices, and critical systems such as AD. These are devices you'll commonly run into during your internal penetration tests, and most times network admins won't bother changing the default credentials. This results in attackers during valid domain credentials which can be leveraged as a stepping stone to obtaining domain admin in a network.
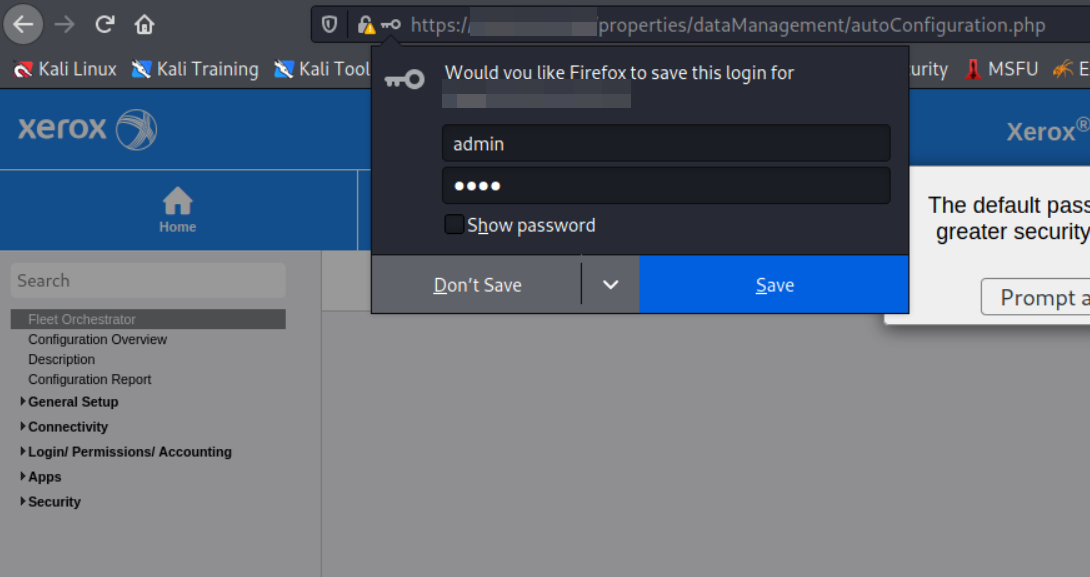
On a recent engagement I found myself inside a clients network with the usual internal software, PBX's, security alarm systems, FTP clients and A LOT of printers. Unfortunately, most were patched and the default passwords changed. All except for the Xerox Printers. The printers on the network were the xerox altalink b8055 and the default password for these are admin:1111
As seen in the image below we were able to successfully authenticate. As a note even if the username and passwords have been changed, its feasible to brute-forced this login as the user will remain admin and the password would typically be easily guessable.
We'll want to then make our way to the Connectivity>Setup page seen below.
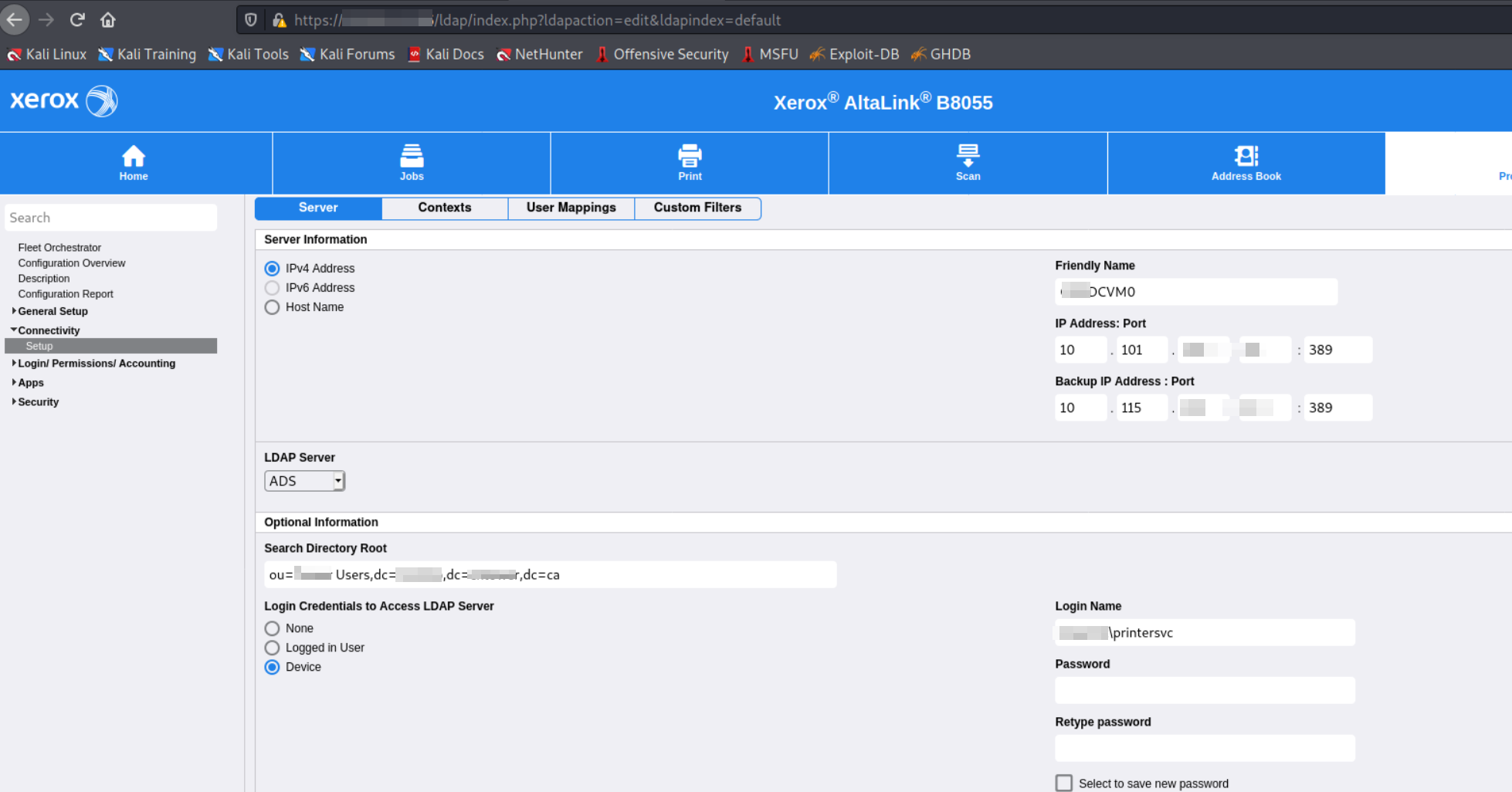
Here is where the LDAP server and utilities is configured and located. We can see that there are 2 LDAP server IP's set 10.101.x.x and 10.115.x.x and if we look at the Login Name we see that a domain joined service account domain\printersvc being used (this is the default service account) for this service.
Our IP is 10.101.112.159 as seen below.
What we'll do is change the IP address of the LDAP server to the IP address of our machine. Therefore, LDAP queries will be passed through us instead of to the server. For those who dont know LDAP is queried in plain text. What we're trying to do here is have the domain\printersvc user authenticate to us via LDAP so that we can recover its credentials in clear text.
As seen above we've changed the IP address of the Xerox's LDAP server to our machine. Once this has been performed we will go to the User Mappings seen below, and and validate that the LDAP server is the IP of our machine. At this point we will leverage the netcat utility to receives the connection which will displays the credentials used by the printer to reach the active directory domain controller, including domain, username and password. Once our netcat listener is setup we will use the LDAP server search field, and search for anything.
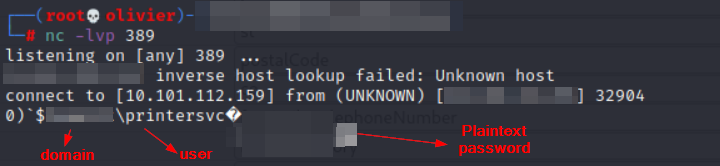
TADA now you've got a domain user and his credentials. From here your job is relatively easy. In the best-case scenario, you've just obtained a AD user account that belongs to privileged security groups.
A sad truth from experience is that these printer service account will typically belong to a privileged group such as "Domain Admins" or "Enterprise Admins" which grants the attacker full control over the Active Directory Domain. Making this typically Medium CVSS finding (default credentials) a critical vulnerability.
If you're unlucky and you're not DA you can still use the domain user to gain a foothold in the domain. For example, given that this is probably not a Red Team, you might as well leverage bloodhound with this service account to obtain a list of all domain users.
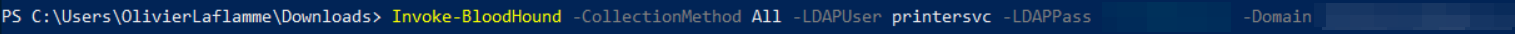
Once the results are obtained you can get the list of domain users with match (u:User) where u.enabled = true return u.name
Now perhaps you've got a list of ~700 domain account that you can happily start spraying with CME. There's no need to do anything fancy you can just spray with passwords like P@$$w0rd, Welcome123, Company2021! and soleil123 If you do this, the odds of you getting a more impactful domain account are HUGE.
This vulnerability is known by Xerox and was identified by Steve Campbell back in Feb of 2020. It is currently vulnerable in the following printers (~80% of all Xerox printers):
Xerox® WorkCentre® 3655*/3655i*/58XX*/58XXi* 59XX*/59XXi*/6655**/6655i**/72XX*/72XXi* 78XX**/78XXi**/7970**/7970i**/EC7836**/EC7856**
As a gentle reminder, this type of vulnerability can be found on most systems that you'll typically encounter on a clients network. So always test for default credentials no matter how silly or unimpactful you think that system may be.

