Using NVIDIA's Leaked Certificate to Improve Anti-Kill
Looking at how signing binaries with leaked Nvidia certificates affect evasion.
Quick little article on how to leverage Nvidia's certificates to lower payload detection in unsophisticated environments. Your implants definitely shouldn't rely on this technique. However, it's nice to see the detection difference from VirusTotal.
Little back story on this. In early 2022 Lapsus$ group leaked a bunch of Nvidia's internal documents. Turns out that the leak contains everything we'd need to sign our binaries on behalf of Nvidia. The following documents were leaked.
We'll use Mimikatz here. First let's get a benchmark by taking Mimikatz and throwing it into VirusTotal. As seen below, 52 AVs are checked and would kill this payload.
So the Nvidia certificates have actually expired, being valid from ~2011-2014. However, Windows will still accept expired certificates. We'll go ahead and use the sign.bat against Mimikatz. When signing as long as we can enter a date within the validity period of the certificate,2014/03/02 for example, you wont run into any issues.
As seen below Mimikatz is now signed by NVIDIA.
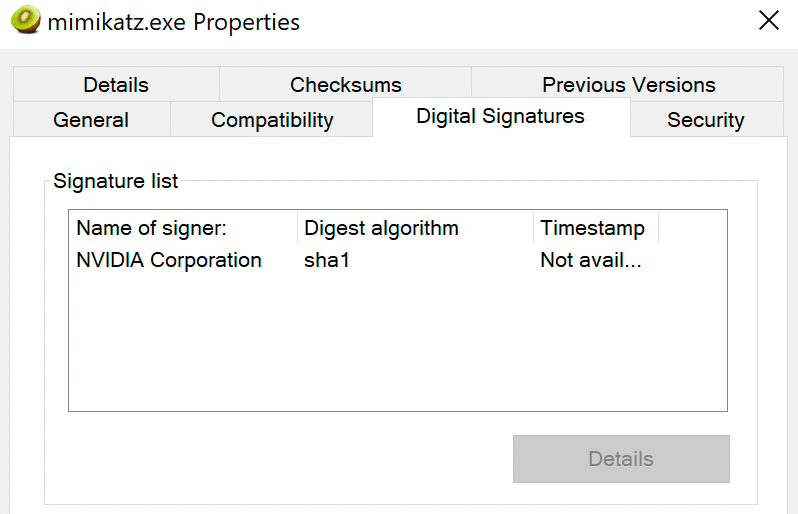
If we throw this version of Mimikatz into VirusTotal 43 AVs are checked and would kill this payload.
It's genuinely not much and again is low-key stone-age methodology. It's only a ~9 AV bypass improvement which for the effort required is not bad.
I would not perform this on my Red Teaming implants, maybe during a regular internal for a clients with poor security posture. The way I see it, you might burn your operation since this might make your executable more suspicious. For starters, your loader should bypass all EDR's and getting it signed by a vendor that could have never been ran within an organization might trigger the EDR's machine learning sensors and models that will flag your process as suspicious. However, there is most likely a lack of telemetry on which this type of detection is built on.
In terms of easily defending against this I stumbled upon a YARA rule addressing signed Nvidia drivers. With some light Googling you'll also be able discover how to to configure Windows Defender Application Control policies to control which Nvidia drivers can be loaded.
To my knowledge this technique is mainly used for malware deployments since digitally signed executables can bypass AV protections. And still signing certificates do not stop anti-malware solutions from recognizing real malware.

