ATM/Kiosk Hacking
Solving the ATM/Kiosk hacking challenges from Positive Hack Days 2021 Payment Village
I'm currently diving into ATM security and I stumbled upon a set of CTF challenges from the Positive Hack Days event held in Moscow last May 2021 as part of the Payment Village.
Disclaimer, I don't speak Russian.
Bankomat1.ova (Difficulty Medium)
- Task: AppLoker bypass & run vbs scripts then escalate your privileges to an administrator.
- Restrictions: Do not use a bootable flash drive.
Upon booting up the VM I was presented with a windows update but to my knowledge, there's nothing that can be leveraged from this alert.
The environment is simply a windows notepad. There is literally nothing else. Presumably, this is simulating the kiosk HTML page that users are typically presented with. For those who don't know, there is no standard that ATM manufacturers adhere too. ATM applications are written in various programming languages, such as C#, C++, Java, and many others. Most of them integrated the GUI in HTML as the primary interface for communication with the client, i.e. the things the client sees on the screen during operations on the ATM. The majority of the screens that a normal user sees during transactions are essentially pure HTML, controlled by one of the above-mentioned applications. These HTML pages are loaded from various service directories.
According to the scenario, the participants have to open the console through a notepad.
I had a few initial ideas before jumping into windows shortcuts and your typical escape paths. The first was to invoke the "HELP" option in notepad which would typically spawn an internet explorer browser. From the browser, we could attempt to map the filesystem and open a file explorer.
Attempting this results in the following message.
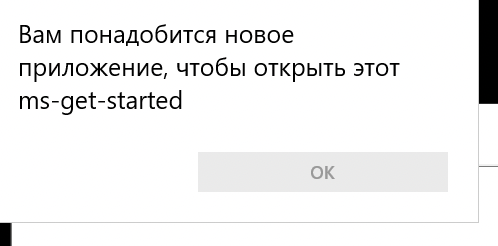
The message box says that "You will need a new application to open this ms-get-started" This got me thinking, am I able to run ms-settings? To do this with a notepad you have to go to Format -> Fonts and click on the "show more fonts" hyperlink.
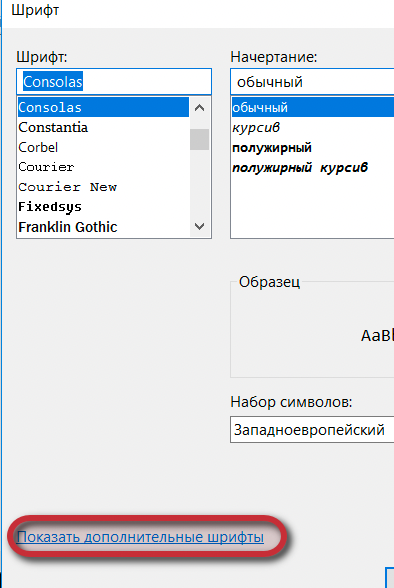
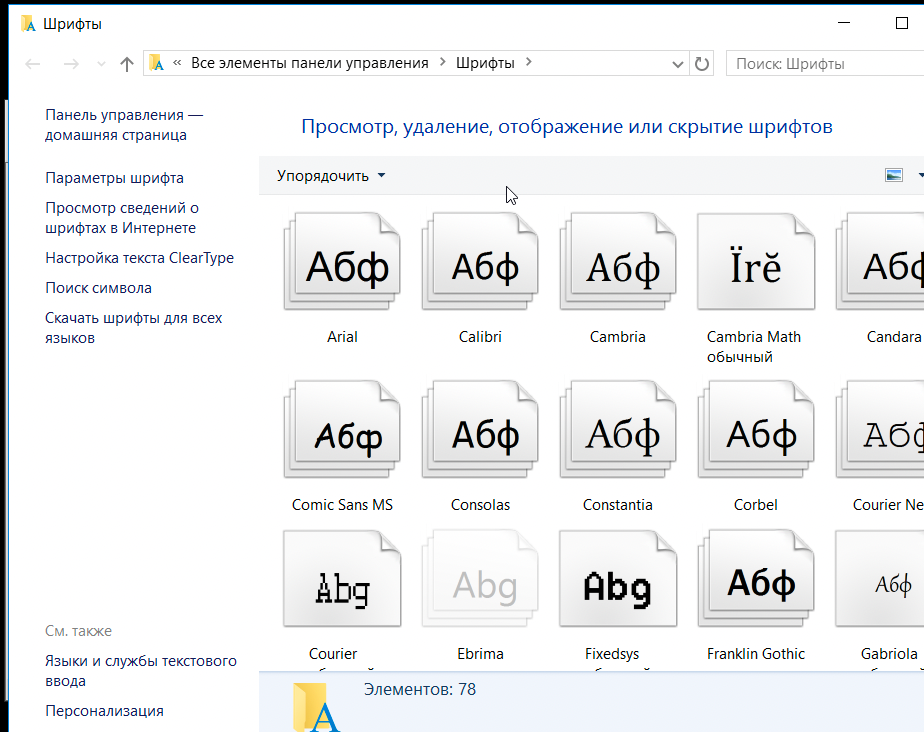
Now, this is good. At least now we have a way to run commands. For those who aren't aware, you can run the command in the file explorer as seen in the figure below.
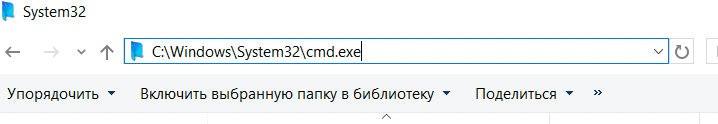
What happens if we run a visual basic script. Obviously, you'll get the following error "An error occurred while executing Windows Script Host. (This program has been blocked by Group Policy. Contact your system administrator for more information.)"
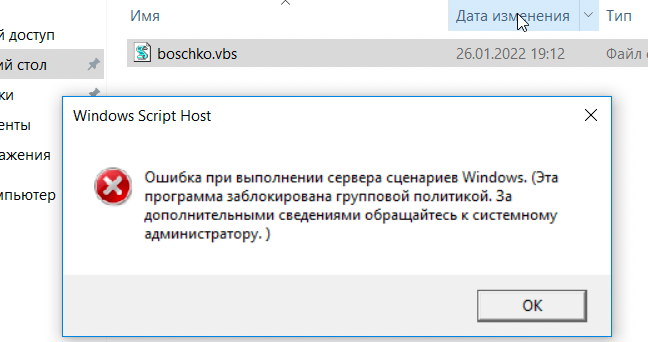
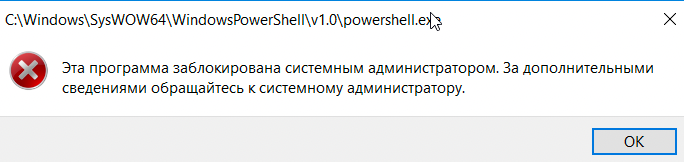
Funny enough powershell.exe is blocked, however, powershell_ise isn't... we won't explore this avenue here but it's something I've never thought of before nor do I think it should work in the first place if AppLocker is properly set.
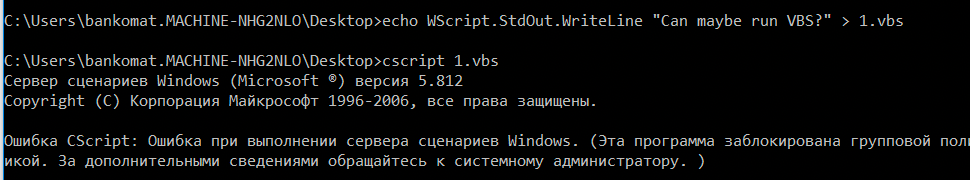
So let's fuck around a little and find out how we can run a visual basic code. Unsurprisingly cscript is blocked.
Since cscript doesn't work chances are wscript won't either. Since hosted scripts are not able to run once on disk perhaps we can leverage mshta and the vbscript: protocol to run simple commands.
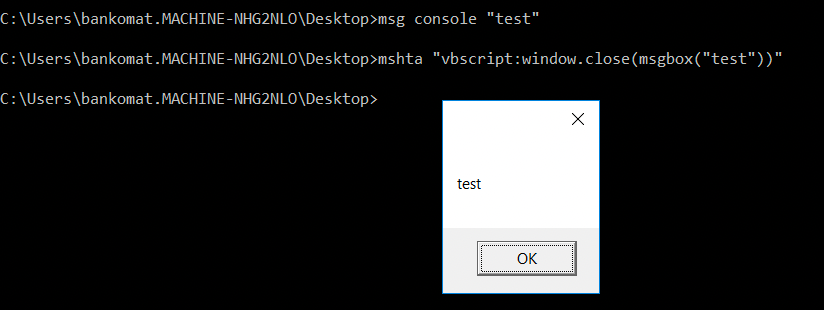
This demonstrated that we're able to run VBS bypassing AppLocker.
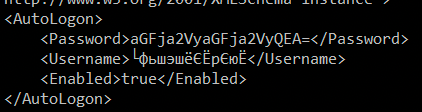
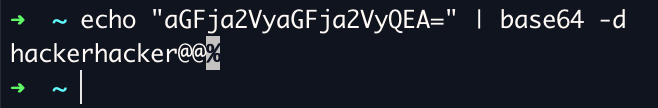
The privilege escalation part had been fucked up because I don't read Russian and google translate sucks when I asked some guys what I was expected to do they said "its on disk"... so I ran findstr /S /M /I /C:"Password" C:\*.* and stumbled onto C:\Windows\Panther\unattend.xml with base64 encoded password. We can open this leveraging visual basic scripting.
Set objFileToRead = CreateObject(“Scripting.FileSystemObject”).OpenTextFile("C:\Windows\Panther\unattend.xml",1)
strFileText = objFileToRead.ReadAll()
objFileToRead.Close
Set objFileToRead = NothingThis file means absolutely nothing to me by the way.
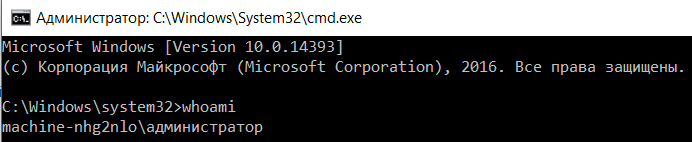
Now we're the administrative user and we've completed this module.
Bankomat2.ova (Hard Difficulty)
- Task: Bypass kiosk mode and somehow elevate privileges on the system to an administrator.
- Restrictions: Do not use a bootable flash drive and safe mode.
Loading the VM and we're presented with the following. Every 5 seconds there is a new "Run" that appears in the terminal. No idea what it does and the client.exe isn't written in C# so I'm not going to spend any time reversing it. It's probably cpp and id rather die than reverse c++.
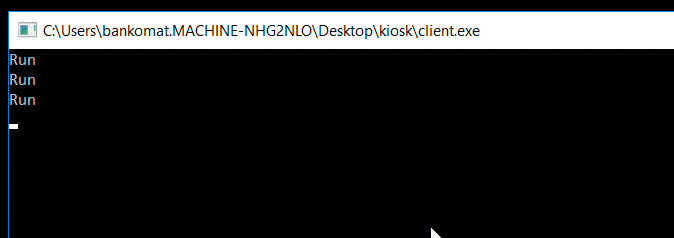
After smashing my keyboard like an ape for ~5 minutes I decided to leverage the lamest escape possible. Sticky keys pop up. All you have to do is hit shift 5 times and voila. As you can see we have a URL we can hit.
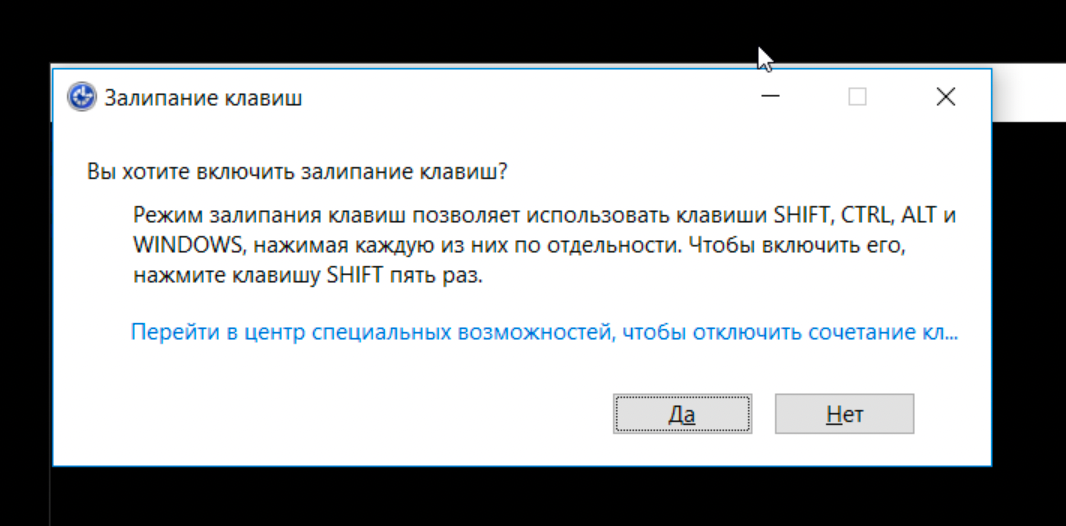
By clicking the link, an instance of settings will be spawned in the background. Then you’ll be simply able to bypass the kiosk. Microsoft has patched this issue by removing the link in newer versions of windows. As it no longer appears when being spawned in a lockscreen environment. I'll go over how to maneuver this later in the blog.
From here we're able to go to the control panel as seen below.
My only problem at this point is that the keyboard is all in Russian. Previously Alt+Shift & Win+Space worked but now it doesn't. After about 30 minutes of fucking around with virtual machines soft keyboards and all that bullshit nothing worked.
Moreover, due to the windows version I cant actually change the keyboard. I can only swap as seen below, and as mentioned above the swapping isn't working.
After a lot more messing around I was able to spawn the windows osk inside the environment where Shift+Alt still didn't work but Alt+Shift+Shift did and so did Win+Space. THANK FUCK.
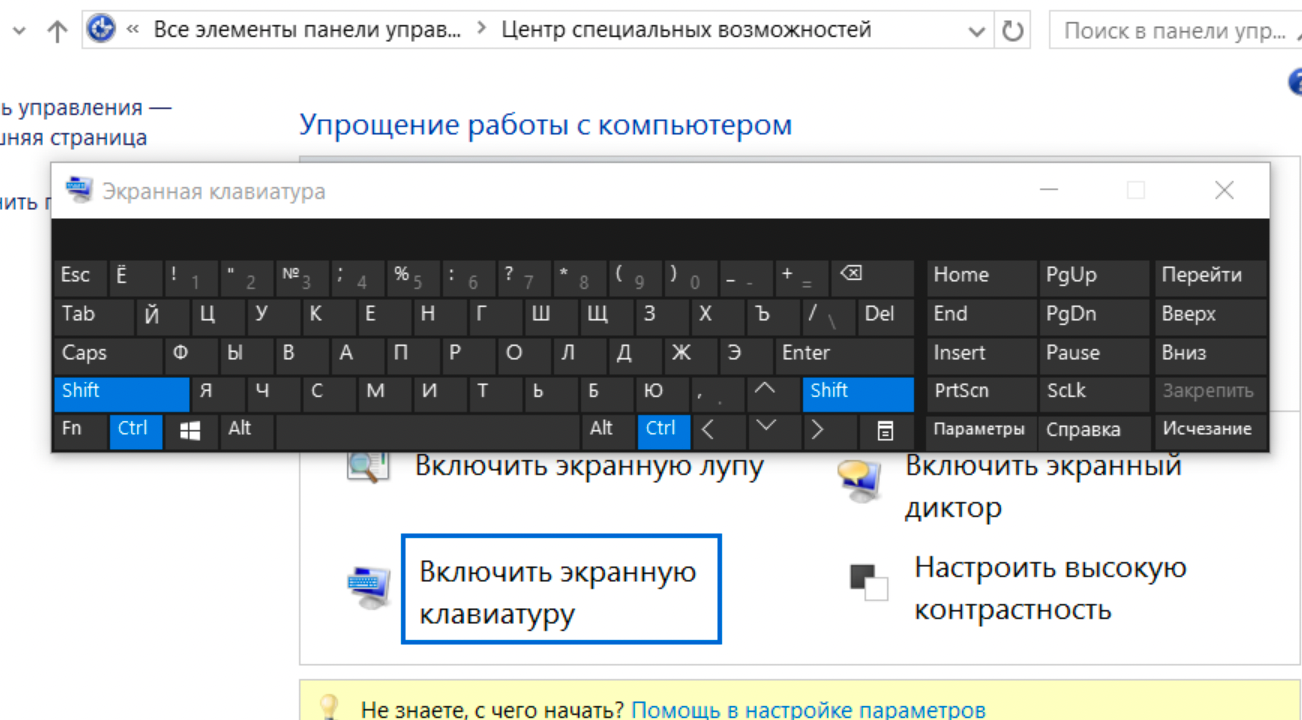
So now we finally have a shell.
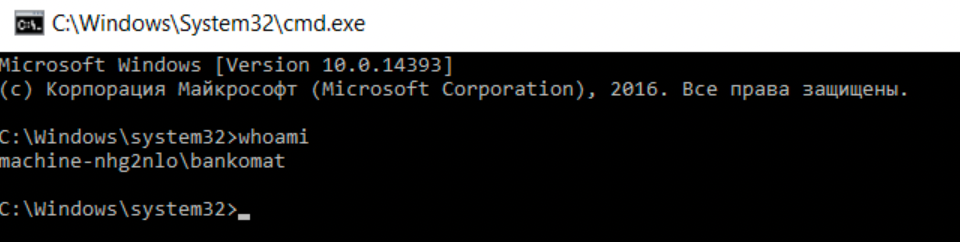
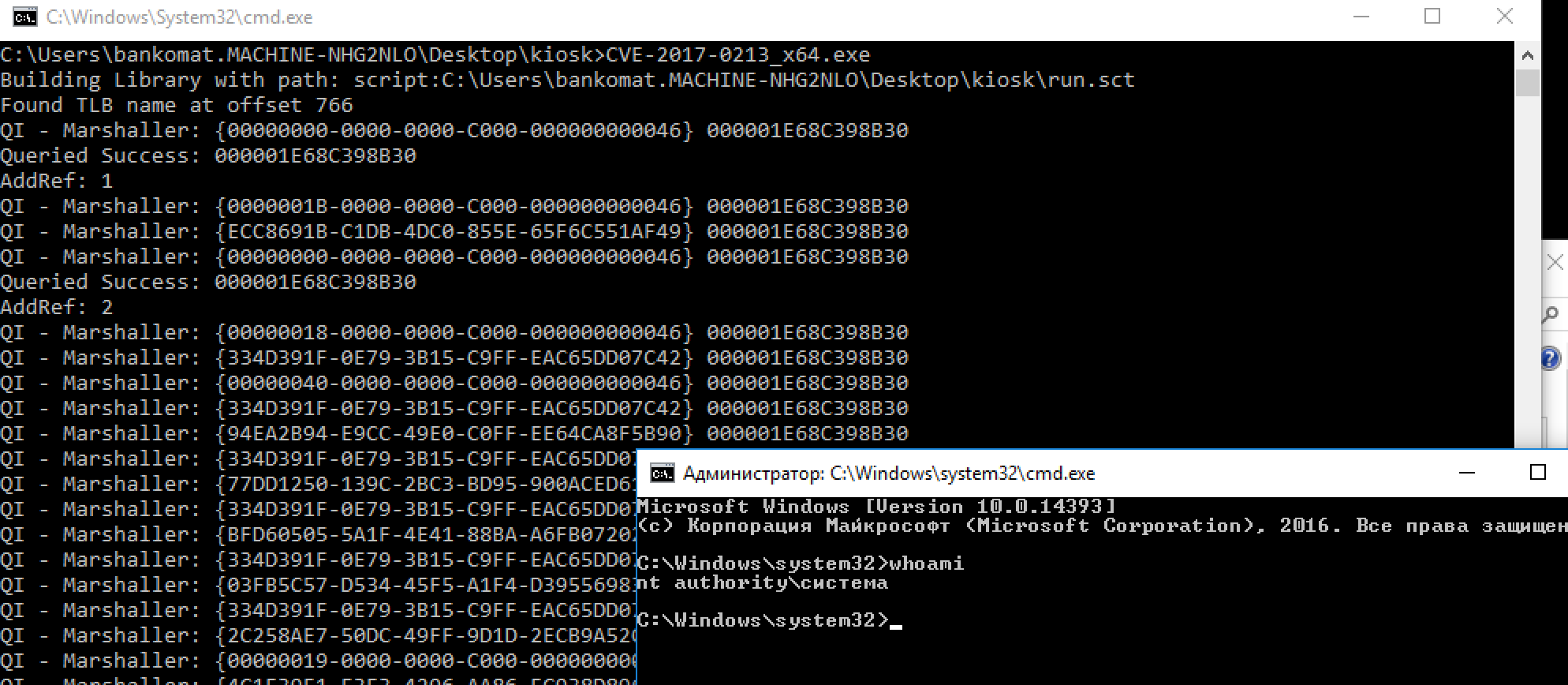
The way to privesc to admin is via CVE-2017-0213 which is an early project zero 0-day. It's a windows COM elevation of privileges. There are a few ways to on-load the binary, first is through a USB and second through a self-hosted web server. Personally, the web server approach didn't work for me, perhaps because I'm using virtualbox.
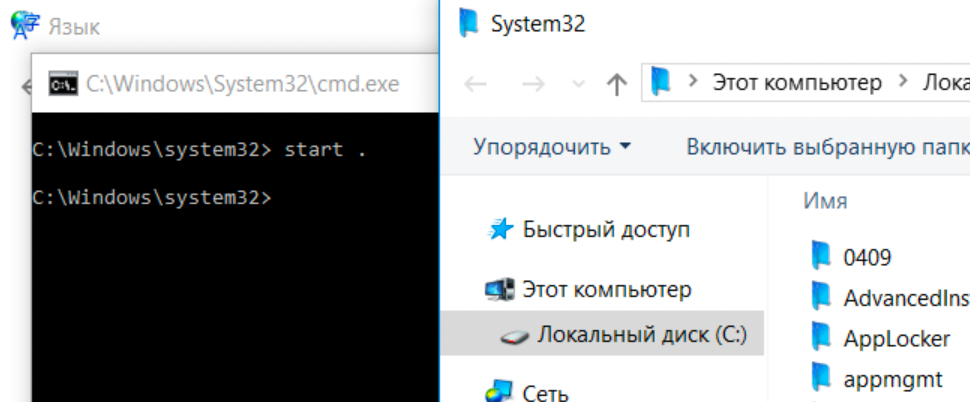
Running start . will open the current path in the file explorer.
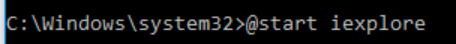
For the web server path just spawn internet explorer via your terminal as seen below.
Drop the executable in the kiosk file location.
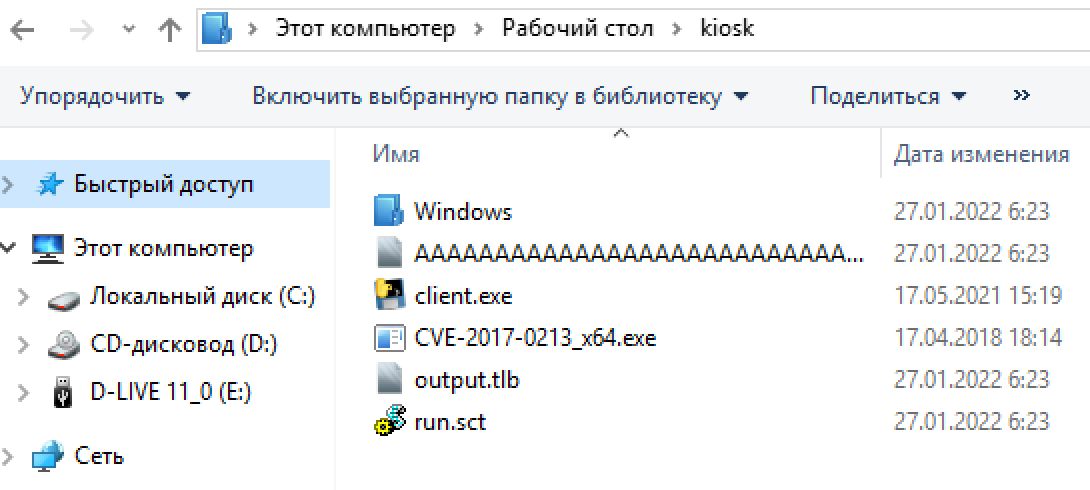
Then its simple just run the EXE and you're NT System :)
Bankomat3.ova (Difficulty Low)
Task: Get out of kiosk mode and somehow elevate privileges to an administrator. Restrictions: Do not use a bootable flash drive.
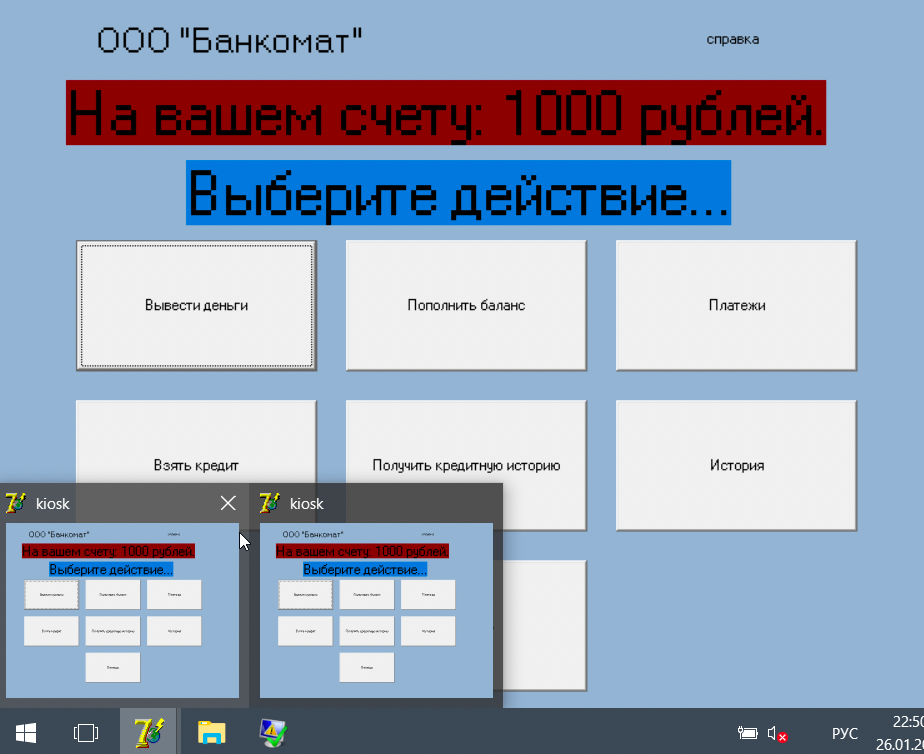
So we'll go ahead and connect to the system, once again we don't have much. When it boots a few interesting things happen. There's about a 1-second window where the desktop is visible and a half a second window where the kiosk spawns but the taskbar remains visible. Few souls are fast enough to click and do anything worth doing in that small period of time.
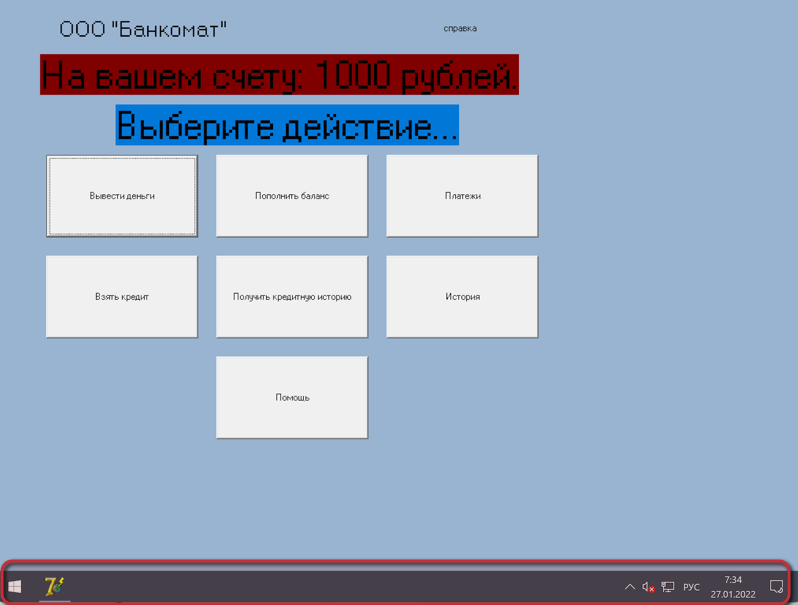
Additionally, I'm not really in the mood to reboot this VM 20 times in a row until I'm fast enough to do shit. I went ahead and tried some ALT, Windows Logo, and Ctrl shortcuts to perform a kiosk escape. But since I'm on a mac and this is a windows system hosted in virtualbox I don't trust that the functionality works properly at all. So let's go back to the good old reliable sticky keys pop-up.
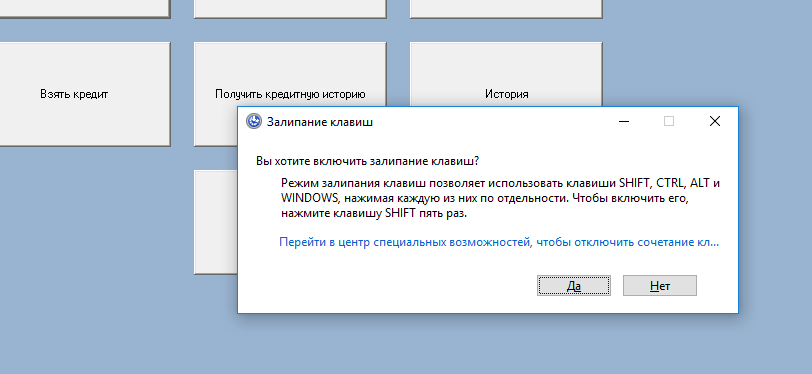
The translation is "Do you want to enable Sticky Keys? Sticky Keys allows you to use the SHIFT, CTRL, ALT, and WINDOWS keys by pressing each one individually. To turn it on, press the SHIFT key five times." and when we click on the hyperlink we aren't redirected. The kiosk still takes precedence over the screen.
We cant activate cortana's "click-text-to-speech" to be able to macgyver our way to a terminal. In the real world when cortana is enabled and we'd click on any button, we would be able to hear the narrator saying “how do you want to open this”, or the name of the location or action we've navigated to using Tab. The narrator’s focus is on something else which is happening outside of the kiosk window. We could typically spawn an “Open With” window with the narrator’s focus on it in the background; Typically the “Open With” window looks like this
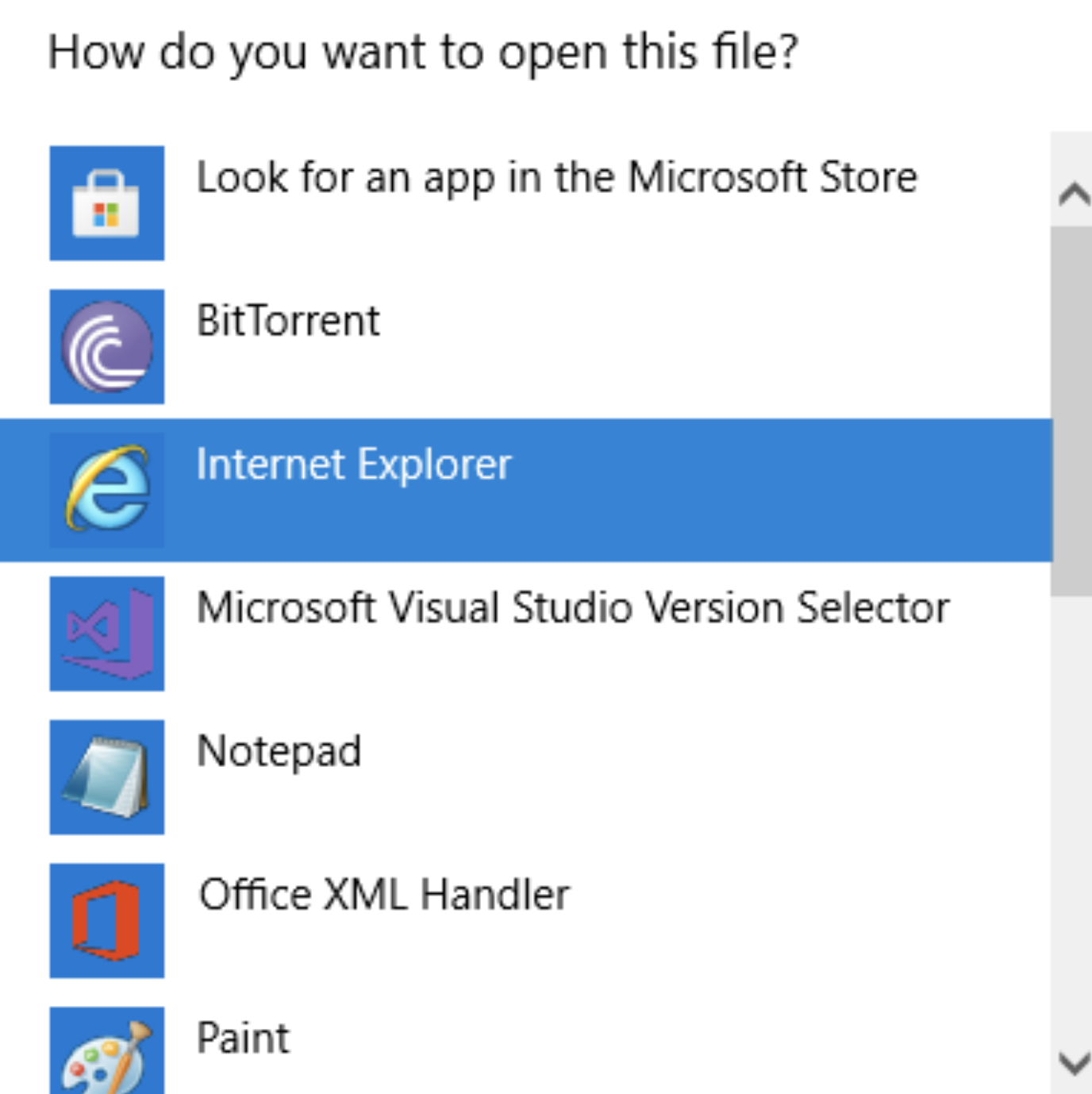
Anyways, we can't do that here. However, the Shift+F10 key is a valid kiosk escape, unfortunately, since I can't read Russian I screwed up and wasn't able to use it again after I unchecked the second to last option.
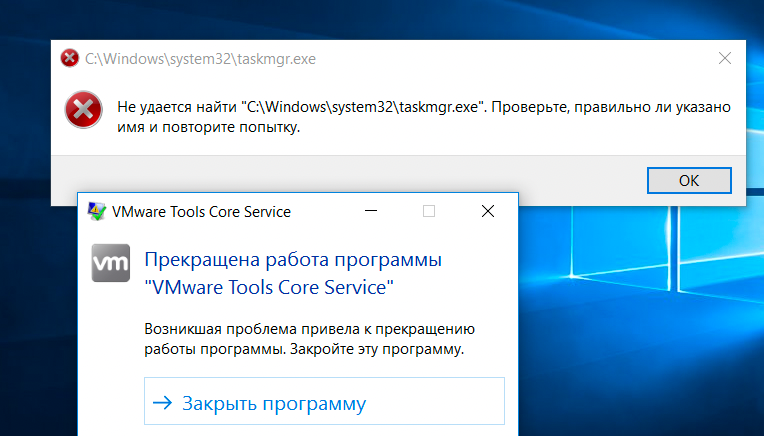
As mentioned above there is a 1.5 second window after the system boost where we'd be able to potentially kiosk escape. It turns out that if we're fast enough, launching taskmanager will cause the system to out error because it can't find the C:\windows\system32\taskmgr.exe which allows us to close the kiosk. If you don't think this is realistic go back to the start of the blog. POS/Kiosks are developed on mushrooms and amphetamines.
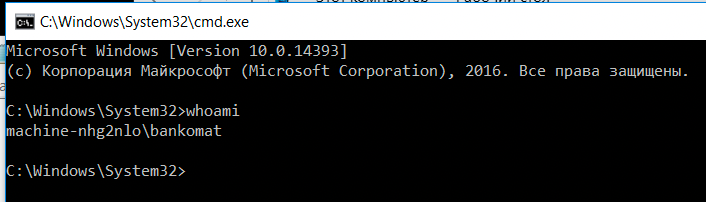
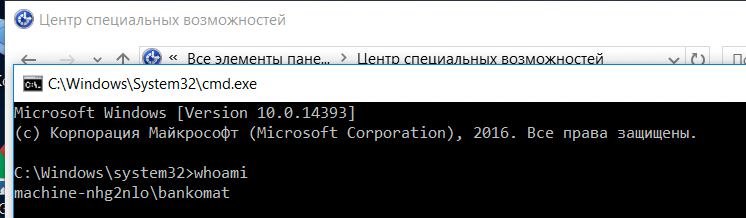
Let's get a cmd and checkout who we are.
So I ended up going to system32 and right-clicking cmd.exe to run as administrator because its SUPER common for ATM local admins to either have their accounts disabled or simply have no password. In our case, we can bypass UAC by leaving the password field blank.
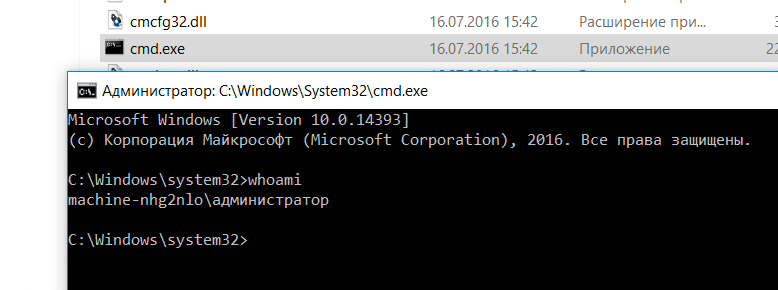
After doing a little more digging you can also bypass the kiosk by booting into safe mode during a system reboot or brake the rules and boot from the media.
If you wanna download the OVA's for yourself go for it they're linked below! I'm sure there are more bypasses and privescs I didn't show of leverage.

